AbstractTargeted companies have minimal leverage to do anything save for agreeing to the troll’s settlement demands or litigating the matter full-tilt.
John F. Luman III and Christopher L. Dodson
Partner and Associate, Bracewell & Giulani, LLP
A coercive patent-holding firm operates a business model that strategically targets firms to force unforeseen patent licensing rents. Coercive patent holders use aggressive litigation tactics to instantaneously create a complicated asymmetrical expensive problem with significant business risk. The strategy creates a dominant position by leveraging legal and business pressure to force the targeted firm into an involuntarily engagement with a coercive patent-holding firm. Such engagements can be quite profitable for the patent holders – and quite devastating for targeted firms. Thus, this article attempts to synthesize a business model framework that reveals insights concerning the profit formula, key resources, and key processes that support the dominant position of coercive patent-holding firms. Based on this framework, we further synthesize countermeasures to disrupt these business model elements and diminish the dominant position. The insights and countermeasures reveal strategic options and tactics that can be leveraged against the business model of a coercive patent-holding firm to alter the dominant position and improve the business situation of the targeted firm.
Introduction
Coercive patent-holding firms assemble an arsenal of patents applicable to specific markets or areas of technology (Fischer & Henkel, 2012). The strategy is to immediately deliver a significant amount of litigation pressure and business risk to a targeted firm and force licensing rents from the firm. A traditional approach to avoid patent infringement against a patent-holding firm is a "freedom to operate" study to identify potentially adverse patents and proactively prepare against potential patent infringement. However, this approach is deficient against coercive patent-holding firms because it is difficult to identify all potentially adverse patents (Pénin, 2012). This difficulty is amplified when dealing with either a strategy of hiding key patents in "thickets" comprising many overlapping patents (Reitzig et al., 2006) or a strategy of continuation patents, where current United States Patent & Trademark Office policy permits a series of patents and additional claims that are re-developed for several years into the future from the filing date of the original patent application. Merges (2009) suggests there is no way to protect against a coercive patent holder, and it is almost impossible to effectively insure against the business risk.
Previous research into coercive patent-holding firms is mixed and discontinuous. Researchers have examined:
- The financial side and wealth transfer from targeted firms (e.g., Bessen et al., 2012; Lu, 2012)
- The makeup and quality of the patent arsenal (e.g., Fischer & Henkel, 2012)
- Firm behaviour and negative labels such as patent trolls, sharks, and non-practicing entities (e.g., Geradin et al., 2011; Layne-Farrar & Schmidt, 2010)
- The relationship to innovation (e.g., Luman III & Dodson, 2006; Merges, 2009; Shrestha, 2010)
- Strategies and business pressure-building tactics (e.g., Columbi & Blasberg, 2006; Tekic & Kukolj, 2013; Togh, 2007)
- Reforming patent office policy (e.g., Burk, 2013; Cotropia, 2009; Luman III & Dodson, 2006)
Previous research reveals two important gaps. There remains no clear formulation of a business model framework for coercive patent-holding firms as it relates to the business model elements and interdependencies between the value proposition, profit formula, key resources, and processes. There are no clear countermeasures focused on these business model elements and interdependencies for altering the dominant position of the coercive patent holder. Countermeasures could enable targeted firms to effectively disrupt the coercive patent holder's business model and diminish their dominant position.
This article makes two contributions. First, it provides a business model framework for coercive patent-holding firms that reveals insights around the elements and interdependencies that create and support the dominant position and customer value proposition. Second, it provides a number of countermeasures that can be leveraged alone or in combination to disrupt the business model elements and interdependencies in a way that alters the dominant position and improves the business situation of a targeted firm relative to the coercive patent-holding firm.
The remainder of this article includes five sections. The first section reviews the literature on coercive patent-holding firms. The second section provides a business model framework for those firms. The third section provides countermeasures against the business model framework; in particular, it outlines tactics and options directed towards key resources, key processes, and the profit formula of coercive patent-holding firms. The fourth section provides recommendations for entrepreneurs and executives. The fifth and final section offers conclusions.
A Review of the Literature on Coercive Patent-Holding Firms
The objective of this literature review is to examine the current state of knowledge concerning coercive patent-holding firms. The relevant literature was located using a broad keyword search of scholarly journals in the Business Source Complete database. The keywords were a combination of: "patent", "troll", "shark", and "non-practicing entity". A close examination of the article abstracts with a focus on coercion revealed a list of 15 articles relevant to coercive patent-holding firms.
The articles covered six different perspectives relating to coercive patent-holding firms:
- Financial aspects (Bessen et al., 2012; Lu, 2012; Pénin, 2012; Reitzig et al., 2007). These articles included aspects of litigation and the relationship to wealth and the stock price of a firm; licensing fees in relationship to over and under payment of rents; the profitability of the business model; and the consequences of R&D investments.
- Patent quality and calibre (Fischer & Henkel, 2012).
- Behaviour of coercive patent-holding firms (Geradin et al.,, 2011; Layne-Farrar & Schmidt (2010)
- Effects on innovation (Luman III and Dodson, 2006; Merges, 2009; Shrestha, 2010)
- Classification and attributes of a firm that litigates patents as a sole source of revenue (Abril & Plant, 2007; Pohlmann & Optiz, 2013)
- Strategies and tactics for and against coercive patent-holding firms (Columbia & Blasberg, 2006; Tekic & Kukolj, 2013; Toth, 2007)
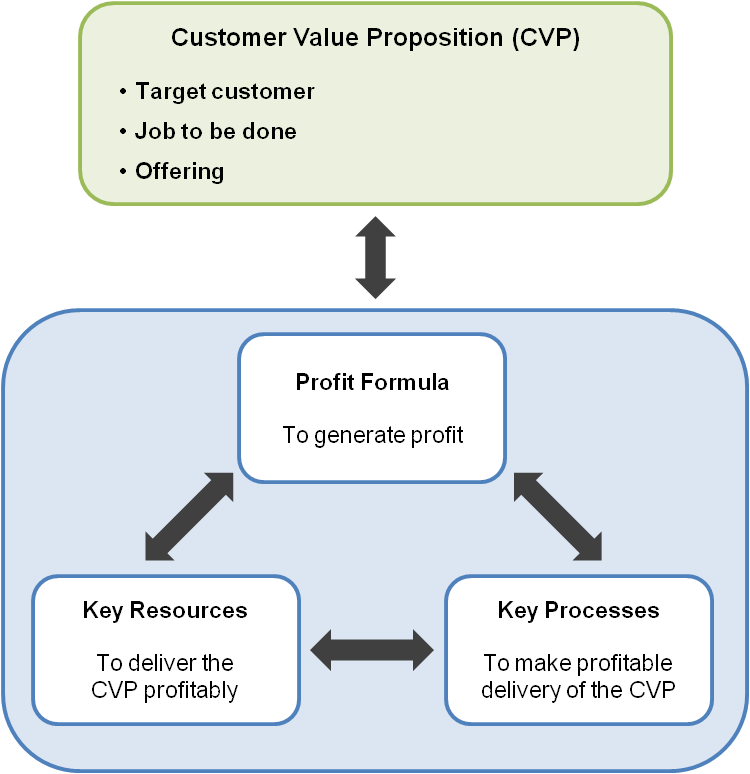
As shown in Figure 1, the general business model framework adapted from Johnson, Christensen, and Kagermann (2008) provides a lens and first perspective to examine the literature from the basic elements of a business model: a customer value proposition, a profit formula, key resources, and processes.
Figure 1. General business model framework (adapted from Johnson et al., 2008)
Examining the literature through the lens of the general business model framework revealed a number of factors and key points associated with each business model element that can be further synthesized into a business model framework for coercive patent-holding firms. Tables 1a through 1d summarize the results and list factors and key points relating to each business model element.
The literature was also examined from a second perspective: that of targeted firm business practices when dealing with coercive patent-holding firms. Examining the literature from the second perspective revealed key points for deficiencies that can be detrimental to the targeted firm and countermeasures that can interfere with the business model elements and interdependencies of the business model framework for coercive patent-holding firms. Tables 2a and 2b summarize the results and lists factors and key points relating to the patent business practices of the targeted firm and potential countermeasures against the business model of coercive patent-holding firms.
Business Model Framework for Coercive Patent-Holding Firms
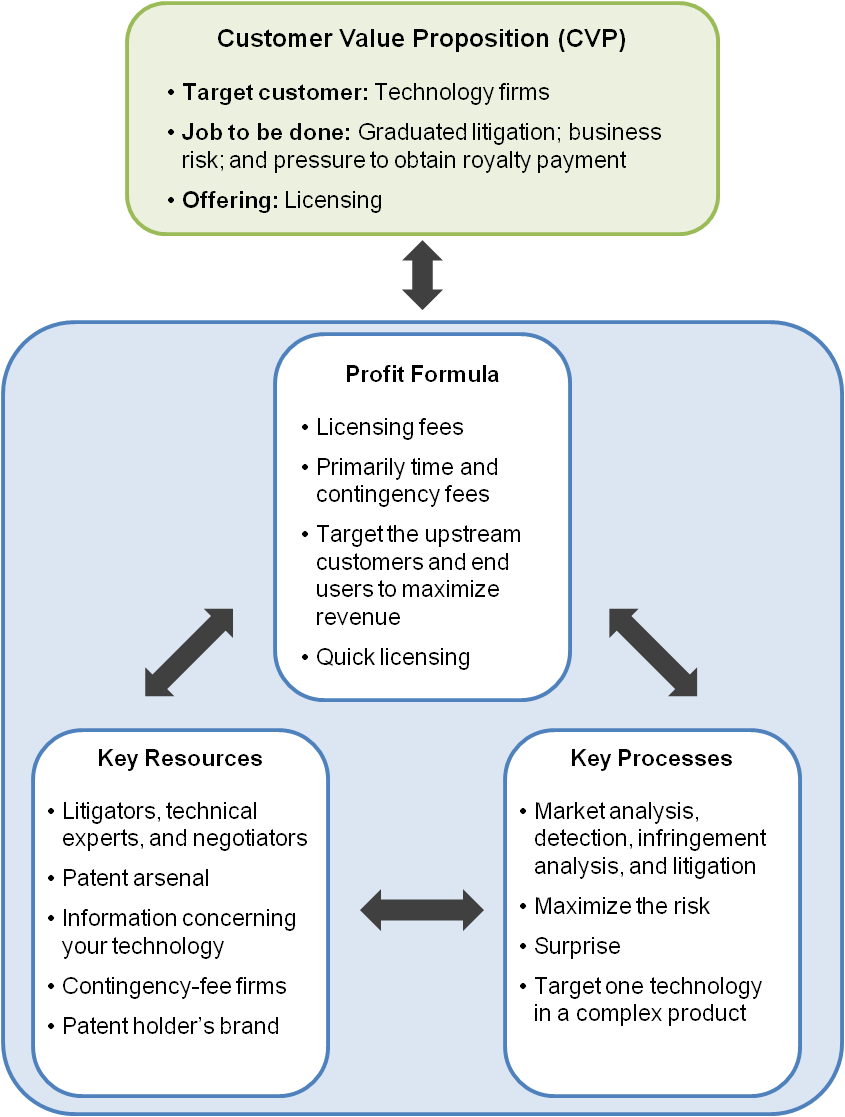
The business model framework for coercive patent-holding firms begins with the general business model framework of Johnson, Christensen, and Kagermann (2008). Then, business model factors and key points from the literature on coercive patent holders are synthesized to form a customer value proposition, a profit formula, key processes, and key resources required to deliver the customer value proposition of coercive patent-holding firms, as shown in Table 3. Figure 2 illustrates the overall framework, and the subsections that follow describe each of the elements in greater detail.
Figure 2. Business model framework for coercive patent-holding firms
Customer value proposition for coercive patent-holding firms
The target customer of a coercive patent-holding firm is another firm, preferably a firm with locked-in or complex technology. These factors increase the business risk for the target customer. The target customer may also be an end user of the technology. The task is to apply graduated patent-litigation pressure and to increase business risk to the technology firm while creating and maintaining a dominant advantage (Luman III & Dodson, 2006). The offering is a licensing fee corresponding to the asserted patents.
Profit formula of coercive patent-holding firms
The revenue model is solely based on patent licensing fees (Layne-Farrar & Schmidt, 2010) such as one-time payments, running royalties, or a combination of both (Fischer & Henkel, 2012; Reitzig et al., 2006; Tekic & Kukolj, 2013; Toth, 2007). The cost structure is primarily determined by time and is preferably based on contingency fees (Abril & Plant, 2007) so that professionals do not receive compensation unless there is a successful license of the patent(s). The margin is based on targeting the upstream value chain, especially with vertically integrated technology, to ensure higher margins for the licensing revenue. Licensing the patent with minimal time, effort, and resources is key to the margin. The licensing revenue can also be proportional to the expense of defending the patent litigation. The resource velocity is preferably fast, with early licensing to minimize the cost structure of time and effort and to enable redeployment of the resources to the next targeted firm.
Key resources
The business model relies upon a blend of litigators, technical experts, and business negotiators. The key asset is the arsenal of patents (Fischer & Henkel, 2012; Merges, 2009) that forms the basis for licensing at least one patent per technology firm. High-level information is initially required concerning the targeted firm's product information. The channels are specific to the technology focus of a coercive patent-holding firm and relate to specific market segments or technologies (Fischer & Henkel, 2012). Partnerships and alliances relate to patent litigation firms to provide a pool of resources on demand. The coercive patent holder's brand varies with the level of success, the total dollar amount of a license, and the business approach to licensing.
Key processes
A market analysis is required to understand the value chain and potential targets for licensing and the timing of licensing (Fischer & Henkel, 2012; Lu, 2012; Lumann III & Dodson, 2006). An analysis is also required to identify and target firms (Lumann III & Dodson, 2006) and any potential for multiple co-defendants (Bessen et al., 2012; Lu, 2012). An initial high-level infringement analysis provides the information required to bring an action for patent infringement. The litigation process is country dependent. A patent reexamination process may be required depending on the response from a targeted firm. Finally, the norms are to maximize litigation pressure and business risk to the targeted firm and to acquire an early dominant position and then maintain it.
Countermeasures That Disrupt the Business Model of Coercive Patent-Holding Firms
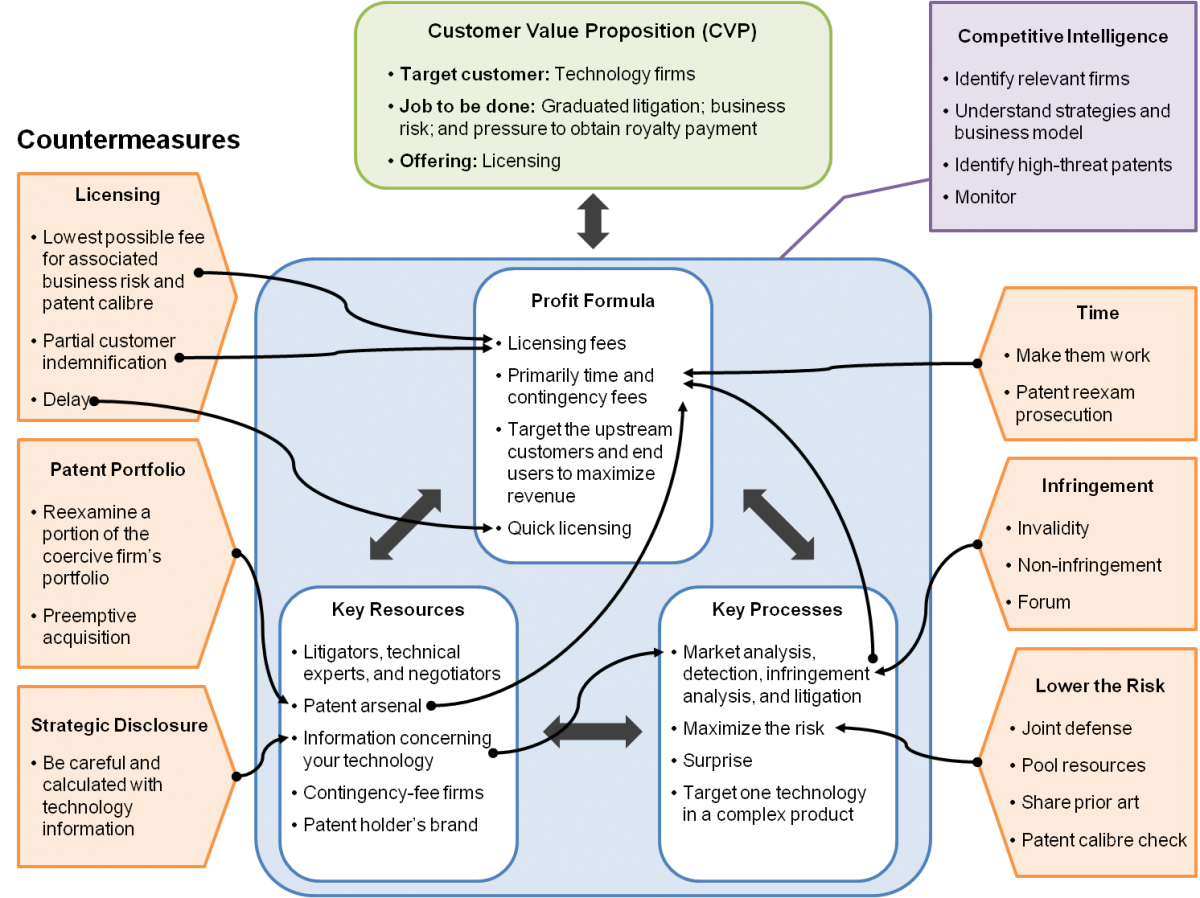
In this section, factors and key points from the literature are synthesized and focused around the profit formula, key processes, key resources, and interactions between these business elements. Countermeasures to disrupt the business model of coercive patent-holding firms are illustrated in Figure 3.
Competitive intelligence countermeasures
Targeted firms must proactively develop competitive intelligence to identify and monitor coercive patent-holding firms active in particular technology markets (Fischer & Henkel, 2012; Pénin, 2012; Reitzig et al., 2006) and the competitive patent landscape. Coercive patent-holding firms are identifiable from their behaviour. They tend to file a lawsuit before any discussion with the targeted firm, the lawsuit is typically based on a number of continuation patents, they keep at least one continuation patent application pending before the patent office, and they select a venue favourable to the coercive patent-holding firm business model, such as the Eastern District of Texas or Delaware. Gathering competitive intelligence removes the surprise factor from the coercive patent holder and the potential for inadvertent infringement (Bessen et al., 2012; Fischer & Henkel, 2012; Reitzig et al., 2011). Once a coercive patent-holding firm is identified for a particular technology market, it may be monitored through the Internet to track patent assets (Reitzig et al., 2006) at the patent office and litigation activity (Geradine et al., 2011). Monitoring the litigation activity may provide an early warning and reveal higher-threat patent assets (Tekic & Kukolu, 2013). An evaluation with respect to the history of the litigated patent and the litigation forum (Toth, 2007) can provide useful insight. Firms should also identify and monitor continuation practice in the United States to determine if additional patent claims are being re-developed. Competitive intelligence also permits an early opportunity to identify, collect, and catalog prior art material against the identified patent assets.
Firms should evaluate identified patents to determine the quality (Geradine et al., 2011; Toth, 2007) or a conduct a hazard analysis from the perspective of infringement (Columbia & Blasberg, 2006) to assist with managerial decisions. Higher-quality patents may suggest quick settlement and lower-quality patents may suggest a longer delay to settlement.
Profit formula countermeasures
Targeted firms can focus on a number of areas in the profit formula of coercive patent-holding firms. A early resolution to the issue with the lowest possible license fee can avoid the business and legal risk and financial expense associated with a patent litigation (Fischer & Henkel, 2012; Toth, 2007). An early license fee before the patent holder spends time and money can reduce the cost of a license fee. Alternatively, a targeted firm can also press forward with the patent litigation, driving up the time and expense for the coercive patent-holder and delaying any potential license fee (Toth, 2007). Driving up the time and expense impacts the profit margin. If there are concurrent litigations with the same patent, the targeted firm can be open and seek early collaboration and information exchange with other defendants (Pénin, 2012) to weaken the patent holder's position and form defense alliances (Columbia & Blasberg, 2006), driving up time and expense for the patent holder. Partial customer patent indemnification can reduce a license fee in some situations by lowering the litigated party's legal expenses associated with a license fee.
Key resource countermeasures
One of the key resources for a coercive patent-holding firm is the patent or portfolio of patents in a particular technology market. Targeted firms have the option to identify and acquire patents to preventing them from becoming a key resource for the coercive patent-holding firm (Toth, 2007). This approach may be undertaken by a single firm alone or in collaboration with other technology firms. A targeted firm may have the patent or patents reexamined (Toth, 2007), driving up time and expense to the patent-holding firm and interfering with its profit formula. Strategic reexamination applied to a select number of patents can tie up and disrupt these patents for several years into the future. Technology firms should be careful with disclosing or releasing confidential information and details surrounding the technology to make it more difficult for the coercive patent-holding firm to identify any potential patent infringement.
The second key resource is people, for example litigators, technical experts, and business negotiators. To further interfere with the profit formula, targeted firms can drive up the amount of time the coercive patent-holding firm must enlist from these people, especially for contingency-fee professionals. The targeted firm can increase the demands for these expensive experts by, for example, delaying the time to achieving a license fee or pressing forward in the patent litigation while continuing to negotiate a license.
Interfering with either or both of these two key resources also interferes with the profit formula in the form of time and expense, especially when contingency fee firms are involved. Litigation can also be disrupted when the patent enters into reexamination.
Key process countermeasures
One of the key processes for a coercive patent-holding firm is the initial infringement analysis and litigation process. The process is designed to maximize the risk to the targeted firm. A targeted firm can assert invalidity of the patent either in the litigation or with the patent office. This assertion also disrupts the profit formula by increasing the amount of time and effort required by the patent holder. A targeted firm can also assert non-infringement of the patent to disrupt the profit formula. Another option is to move the litigation to a more favourable forum (Toth, 2007) and consider a joint defense to pool resources. A more favourable forum is a jurisdiction that historically tends to render decisions in favour of defendant and at the expense of the patent holder.
There are also technology options to lower the risk. One option is to design around the patent (Fischer & Henkel, 2012; Layne-Farrar & Schmidt, 2010; Reitzig et al., 2006) and limit the future risk of licensing fees and infringement. Firms should keep their technology options open (Reitzig et al., 2006; Toth, 2007) to lower the future risk associated with infringement. They can remove dependencies on particular technologies (Reitzig et al., 2006), identify a range of alternate technologies and substitute technologies (Reitzig et al., 2006), and build a modular architecture to permit rapid change (Pénin, 2012). However, firms should exercise caution when using or incorporating third-party technology (Columbia & Blasberg, 2006), especially standards-based technology.
Figure 3. Countermeasures and their impacts on the business model elements of coercive patent-holding firms
Recommendations for Entrepreneurs and Executives
From a close reading of the published research on coercive patent-holding firms; through induction and synthesis focusing on the targets, revenue stream, patent arsenal, targeted firm oversights, strategies, countermeasures, and calibre of patents from coercive patent-holding firms; and drawing upon the author's practical experience as an intellectual property management consultant and patent agent, five recommendations are offered for entrepreneurs and executives seeking to be prepared and ready to deal with a coercive patent-holder.
1. Proactively gather relevant competitive intelligence about coercive patent-holding firms.
Identify coercive patent-holding firms that are relevant to your technology market and business. This is no different than identifying competitors and customers relating to your technology company. Once you compile a list of relevant patent-holding firms, identify the patents of interest to your technology or business. To gather relevant competitive intelligence, monitor the activities of the patent-holding firms, the patents of interest, and key litigations against competitors or end users. Find and track relevant prior art technology, and make use of Internet information portals relating to coercive patent-holding firms. These activities must be done as early as possible and on an ongoing basis so that you are prepared for any engagement by a patent holder.
2. Be prepared to disrupt the profit formula of a coercive patent-holding firm.
The profit formula may be disrupted directly or indirectly through the key resources and key processes. Take advantage of an early resolution of the litigation with the lowest possible fee before the patent holder spends time and money driving up the license fee. Alternatively, delay the resolution and drive up the time and expense to make a tradeoff with the license fee while lowering the margin of the coercive patent-holding firm.
3. Have a strategy to disrupt the key patent resource.
The key patent resource may be disrupted through a patent reexamination procedure. The larger the number of patents placed into a reexamination procedure, the larger the disruption to the key patent resource. This disruption will continue for several years. Disrupting the key patent resource also indirectly disrupts key processes concerning litigation, infringement, and validity as well as indirectly disrupting the profit formula by increasing time and expense while lowering the margin. A strategy to disrupt one or more patent resources increases the patent holder's time and expense while lowering the profit margin and can be helpful in negotiating a lower licensing fee. Minimal risk with a maximum disruption can occur when you target patents that cannot be asserted against your business or technology. Another option is to target patents that cannot be asserted against you and are in active litigation against other firms.
4. Know the calibre of the patent held by the coercive firm.
Assessing the quality or calibre of the asserted patent provides valuable information and insight in support of business decisions. Smith (2014) provides a comprehensive review of citation-based patent evaluation methodologies that may be applied to evaluate a patent. A high-calibre patent suggests a business decision towards seeking an early business solution.
5. Ensure you have a flexible technology architecture.
A flexible and modular technology architecture helps reduce risk and provides options. Identify and keep a range of alternate and substitute technology modules available that may replace portions of the technology architecture. Be careful with integrating or relying upon third-party technology, especially technology based on industry standards.
Conclusion
This article focused on developing a business model framework for coercive patent-holding firms that reveals insight into the business model elements and interdependencies required by the profit formula, key resources, and processes to deliver the customer value proposition. This article also provides a range of countermeasures against the profit formula, key resources, and processes to disrupt the business model of coercive patent-holding firms. Leveraging these countermeasures against a coercive patent holder provides strategic and tactical advantage to disrupt the business model of such a firm and improve the business situation of the targeted firm. Entrepreneurs and executives can leverage these countermeasures to directly raise the adversary’s business risk by disrupting a combination of key business elements to alter the dominant position of a coercive patent-holding firm.
Policy makers need to re-think the rules governing continuation practice in the United States and address the inequity of permitting a patentee the opportunistic ability to re-develop patent claims from an old patent application based on direct reference to present day technology. In parallel with this policy issue, firms need to re-think the business practice applied to avoid and defend against patent infringement. A freedom-to-operate approach involves searching databases for relevant patents in a particular area of business or technology. This older approach is limited in that it is very difficult to find all the relevant patents, and coercive patent-holding firms tend to hide patents by assigning patents to many different company names. Firms could transform the behaviour from a freedom-to-operate approach that is limited against coercive patent holders to that of a strategic countermeasure approach that targets the business model of coercive patent holders to alter their dominant position.
Further research should focus on refining the understanding of the business model of coercive patent-holding firms in the areas of the profit formula, key resources, and processes. Further research should also examine case studies of targeted firms that have successfully disrupted the business model of coercive patent-holding firms, specifically examining how they disrupted the interactions between the profit formula, key resources, and processes.
Entrepreneurs and executives must be ready for the day when they become unwillingly engaged with a coercive patent-holding firm. They must identify and monitor patent holders related to their market and technology segment. By proactively targeting and be prepared to disrupt the business model of a coercive patent-holding firms, firms can overcome the threat they represent.
Table 1a. Customer value propositions of coercive patent-holding firms: factors and key points
|
Factors |
Key Points |
|
Target Customers |
|
|
Job to Be Done |
|
|
Offering |
|
Table 1b. Profit formula of coercive patent-holding firms: factors and key points
|
Factors |
Key Points |
|
Revenue Stream |
|
|
Cost Structure |
|
|
Margin Model |
|
|
Resource Velocity |
|
Table 1c. Key resources of coercive patent-holding firms: factors and key points
|
Factors |
Key Points |
|
Patent Arsenal |
|
|
Calibre of Patent Arsenal |
|
Table 1d. Key processes of coercive patent-holding firms: factors and key points
|
Factors |
Key Points |
|
Litigation Analysis |
|
|
Market Analysis |
|
|
Maximize the Risk |
|
|
Strategy |
|
Table 2a. Deficiencies in the business practices of targeted firms that enable the business models of coercive patent-holding firms: factors and key points
|
Factors |
Key Points |
|
Competitive Intelligence |
|
|
Patents |
|
|
Technology Architecture |
|
Table 2b. Potential countermeasures against the business models of coercive patent-holding firms: factors and key points
|
Factors |
Key Points |
|
Competitive Intelligence |
|
|
Patents |
|
|
Technology Architecture |
|
|
Litigation |
|
Table 3. Synthesizing a business model framework for coercive patent-holding firms from a general business model framework
|
Elements |
General Business Model Framework |
Business Model Framework for Coercive Patent-Holding Firms |
|
Customer Value Proposition |
Target Customer Job to be done Offering |
Technology firms Graduated litigation, business risk, and pressure to obtain a royalty payment Licensing |
|
Profit Formula |
Revenue model Cost structure Margin model Resource velocity |
Licensing fees Low-cost patents & professional time Minimize time & maximize license value Early licensing |
|
Key Resources |
People Technology; products Information Partnerships; alliances Brand |
Litigators, technical experts & negotiators Patent arsenal Information concerning your technology Partner and alliance with patent litigators and other intellectual property professionals Brand of coercive patent holder brand |
|
Key Processes |
Processes Rules and metrics Norms |
Market analysis, detection, minimal infringement analysis, litigation Wait or delay Surprise Target one technology in a complex product Target maximum risk |
References
Abril, P. S., & Plant, R. 2007. The Patent Holder’s Dilemma: Buy, Sell or Troll? Communications of the ACM, 50(1): 37–44.
http://dx.doi.org/10.1145/1188913.1188915
Bessen, J., Ford, J., & Meurer, M. M. 2012. The Private and Social Costs of Patent Trolls: Do Nonpracticing Entities Benefit Society by Facilitating Markets for Technology? Regulation, 34(4): 26–35.
Burk, D. L. 2013. Patent Reform in the US: Lessons Learned. Regulation, 35(4): 20–25.
Cotropia, C. A. 2009. The Individual Inventor Motif in the Age of the Patent Troll. Yale Journal of Law and Technology, 12(1): 53–84.
Columbia, S. C., & Blasberg, S. T. 2006. Beware Patent Trolls. Risk Management, 53(4): 22–27.
Fischer, T., & Henkel, J. 2012. Patent Trolls on Markets for Technology – An Empirical Analysis of NPEs’ Patent Acquisitions. Research Policy, 41(9): 1519–1533.
http://dx.doi.org/10.1016/j.respol.2012.05.002
Geradin, D., Layne-Farrar, A., & Padilla, A. J. 2011. Elves or Trolls? The Role of Nonpracticing Patent Owners in the Innovation Economy. Industrial and Corporate Change, 21(1): 73–94.
http://dx.doi.org/10.1093/icc/dtr031
Johnson, M. W., Christensen, C. M., & Kagermann, H. 2008. Reinventing Your Business Model. Harvard Business Review, December 2008: 57–68.
Layne-Farrar, A., & Schmidt, K. M. 2010. Licensing Complementary Patents: Patent Trolls, Market Structure, and Excessive Royalties. Berkeley Technology Law Journal, 25: 1121–1143.
Lu, J. 2012. The Myths and Facts of Patent Troll and Excessive Payment: Have Nonpracticing Entities (NPEs) Been Overcompensated? Business Economics, 47(4): 234–249.
http://dx.doi.org/10.1057/be.2012.26
Luman III, J. F., & Dodson, C. L. 2006. No Longer a Myth, the Emergence of the Patent Troll: Stifling Innovation, Increasing Litigation, and Extorting Billions. Intellectual Property & Technology Law Journal, 18(5): 12–16.
Merges, R. P. 2009. The Trouble with Trolls: Innovation, Rent-Seeking, and Patent Law Reform. Berkeley Technology Law Journal, 24(4): 1583–1614.
Pénin, J. 2012. Strategic Uses of Patents in Markets for Technology: A Story of Fabless Firms, Brokers and Trolls. Journal of Economic Behavior & Organization, 84(2): 633–641.
http://dx.doi.org/10.1016/j.jebo.2012.09.007
Pohlmann, T., & Opitz, M. 2013. Typology of the Patent Troll Business. R&D Management, 43(2): 103–120.
http://dx.doi.org/10.1111/radm.12003
Reitzig, M., Henkel, J., & Heath, C. 2007. On Sharks, Trolls, and Their Patent Prey – Unrealistic Damage Awards and Firms’ Strategies of “Being Infringed”. Research Policy, 36(1): 134–154.
http://dx.doi.org/10.1016/j.respol.2006.10.003
Shrestha, S. K. 2010. Trolls or Market-Makers? An Empirical Analysis of Nonpracticing Entities. Columbia Law Review, 110: 114–160.
Smith, D. K. W., 2014. A New Methodology for Citation Dependent Patent Evaluations. Ottawa, Canada: Carleton University.
http://curve.carleton.ca/system/files/theses/31557.pdf
Tekic, Z., & Kukolj, D. 2013. Threat of Litigation and Patent Value: What Technology Managers Should Know. Research-Technology Management, 56(2): 18–25.
http://dx.doi.org/10.5437/08956308X5602093
Toth, J. M. 2007. Fighting Back against Patent Trolls. Inside Counsel, 17: 20–21.
Keywords: business model, business model framework, coercive patent holder, countermeasures, intellectual property, non-practicing entity, NPE, patent, patent arsenal, patent office policy, patent shark, patent troll